It has been absolutely ages since I have written a blog post – genuinely I really havent simply been slacking off, i’ve just been busy! Anyway, figured it was time to do a writeup on some stuff I have been working on. (Please note this is almost the exact same post from the Paterva blog).
Predominately I want to show you some of the work we had to do for Blackhat 2013 – my first BH talk ever! My section of the work was what we ended up calling ‘KingPhisher’ as well as the multi-threaded Python script to crawl websites for some parts of ‘Teeth’ (Roelof’s offensive Maltego transforms).
<TL;DR>
Video: [http://www.youtube.com/watch?v=QS5zgFKzLhs&feature=c4-overview&list=UUThOLpqhLFFQN0nStdkyGLg]
Download: [http://www.paterva.com/BlackhatUSA2013/]
</TL;DR>
A common Paterva office treat is that if you make a mistake or if the other person can catch you out at anything you have to make tea (the amount of times I make tea is inversely proportional to how long I have been at Paterva!). This included phishing. Many years ago we would try trick each other into clicking on links. Most security people will agree with us when we say that if you have enough context on a person you can craft an email and include a link on which they *will* click. Additionally we have used Maltego to gain context on people for a while, specifically using social networks (including transforms provided commercially via the SocialNet package). We also accept that there are certain types of mail we seldomly check (in terms of headers/other), we have been semi-programmed by automatic spam filtering and anti-virus to notify us if something is bad. Bottom line — we don’t inspect every link on every mail and we doubt if you do too.
So with this in mind we decided to integrate the two sides – 1) targeted phishing attacks and 2) information gathering in Maltego.
The first _really_ exciting part for me is that we took the first steps towards protocol 3, what’s known as graph in/graph out. In this case it was just sending the graph out, but it meant that we could finally receive context on the entities sent to transforms! It uses the new ‘Send to URL’ transform that POSTs the graph data in XML to a specific script (e.g. http://zer0cool.tld/graphin.php). This script then returns a URL to Maltego which in turn starts a browser with that page. What this gives you is the ability to do customised exporting of data for things like viewing graphs online, reporting or doing additional data mining based on context (NOTE: There is a limit of 50 entities for this ‘transform’).
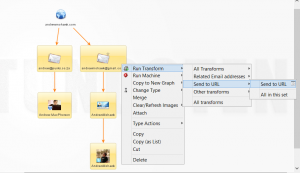
Please note I have added this transform to a set so that I dont need to go find it. (Sets can be managed under the manage tab->Manage transforms)
The first section tackled was the Maltego side of things which has been done before. You can give it a go yourself within the tool or watch our videos. Having context on the graph means you can do something like Person->Email->social network membership. It means you know a) the a persons name, b) you know their email address and you know they use it for social networking and c) you know what their social network profile is. From the social network you can mine for particular types of information that you can leverage for the phishing attack.
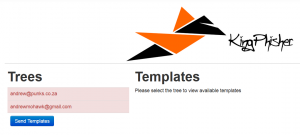
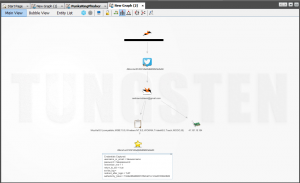
In the above example we see that andrew@punks.co.za relates to my Facebook account and that I use andrewmohawk@gmail.com for my Twitter account with an Alias ‘AndrewMohawk’.
This takes us to the second part – the KingPhisher web application. This web application is made up of the following sections:
* The ‘receiver’ accepts the POST of the graph from Maltego and stores it in a local sqlite database, then returns a URL to Maltego which is automatically opened.
* The ‘wizard’/interface. This is the wizard/interface that will be used to craft templates based on information available in the graph.
* The ‘sender’. This is merely a PHP SMTP script that you can move around to send the actual mail. It ensures you can keep the wizard/main interface separate from the machine you send mail from.
* The ‘catchers’. These are fake websites used to attempt to capture credentials (where needed).
The receiver parses all the XML and works out what is connected into ‘trees’ that compromise of a parent and N children – where at least one of the entities, either parent or child – is an email address.
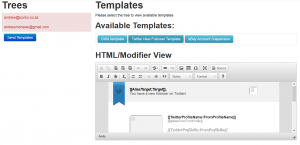
The Wizard will look at the ‘trees’ and figure out which templates are available for use. As an example, if a tree has a Facebook profile we can use a Facebook template as well as generic ones that don’t require additional context and if it had a Twitter account we could use a template relating to Twitter as well as the generic templates.
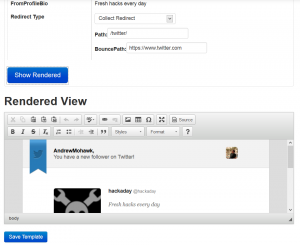
Once you have selected a particular tree and a template you can then configure it. Each template has one standard configuration option that determines how the link would behave. The options are:
1. Clean redirect – simply changes the link to a location you have selected.
2. Bounce redirect – changes the link to a KingPhisher ‘catcher’ which once browsed to will redirect the target to a user selectable location. It will also capture and store the user agent and IP address.
3. Collect – This will redirect to a catcher that will look like a legitimate website. It also captures the user agent and IP address as well as any credentials entered into the fake website. In future these sites could/should be made a little more intelligent by only serving sites if the target is coming from the correct IP range or serving different websites based on the user agent.
The wizard screens are shown below:
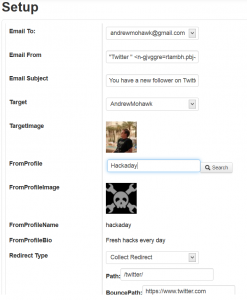
The template settings for the Twitter template where the “fromProfile” field has been entered by the attacker
Once the templates have been selected and configured they can be viewed and saved. When everything is fine tuned the emails can be sent out to the targets. The sending process is routed via the ‘sender’ script which can either live on the same machine as the interface/wizard or anywhere else on the Internet.
Getting templates into the actual mailboxes without them hitting spam filters proved particularly difficult as there were 3 main things that common email providers seemed to look for:
1. SPF/DKIM for the domain you were using for the spoof address – this means no email from *.facebook.com, *.twitter.com etc.
2. The DOM markup of each template (if it was too similar to the original one it was flagged) — so no stealing of templates.
3. Particular phrases within templates – this was probably the trickiest to get around as often it was strings like company address or name. It took a few runs to get it right!
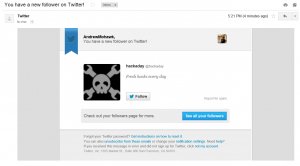
Once we had got around these (you can see the email addresses and templates we use in the code) the mails were delivered to the inboxes of our targets (in this case my Gmail account):
After this process has been completed the attackers can then sit back and enjoy watching their Maltego machine run. The machine will query the KingPhisher server for campaigns (emails sent out), then retrieve those email addresses and any additional information (UA/IP for ‘bounce’ type links and the posted fields/other collected data for the ‘collect’ type links).
The sequence of transforms in the machine are shown below:
At this stage the user has not entered any details into the fake site, merely opened it and his/her UA and IP are collect
To get KingPhisher you can go to http://www.paterva.com/BlackhatUSA2013/ and download the ZIP package. Inside the ZIP are a number of documents relating to installation as well extending the interface, creating templates and so on. Have fun!