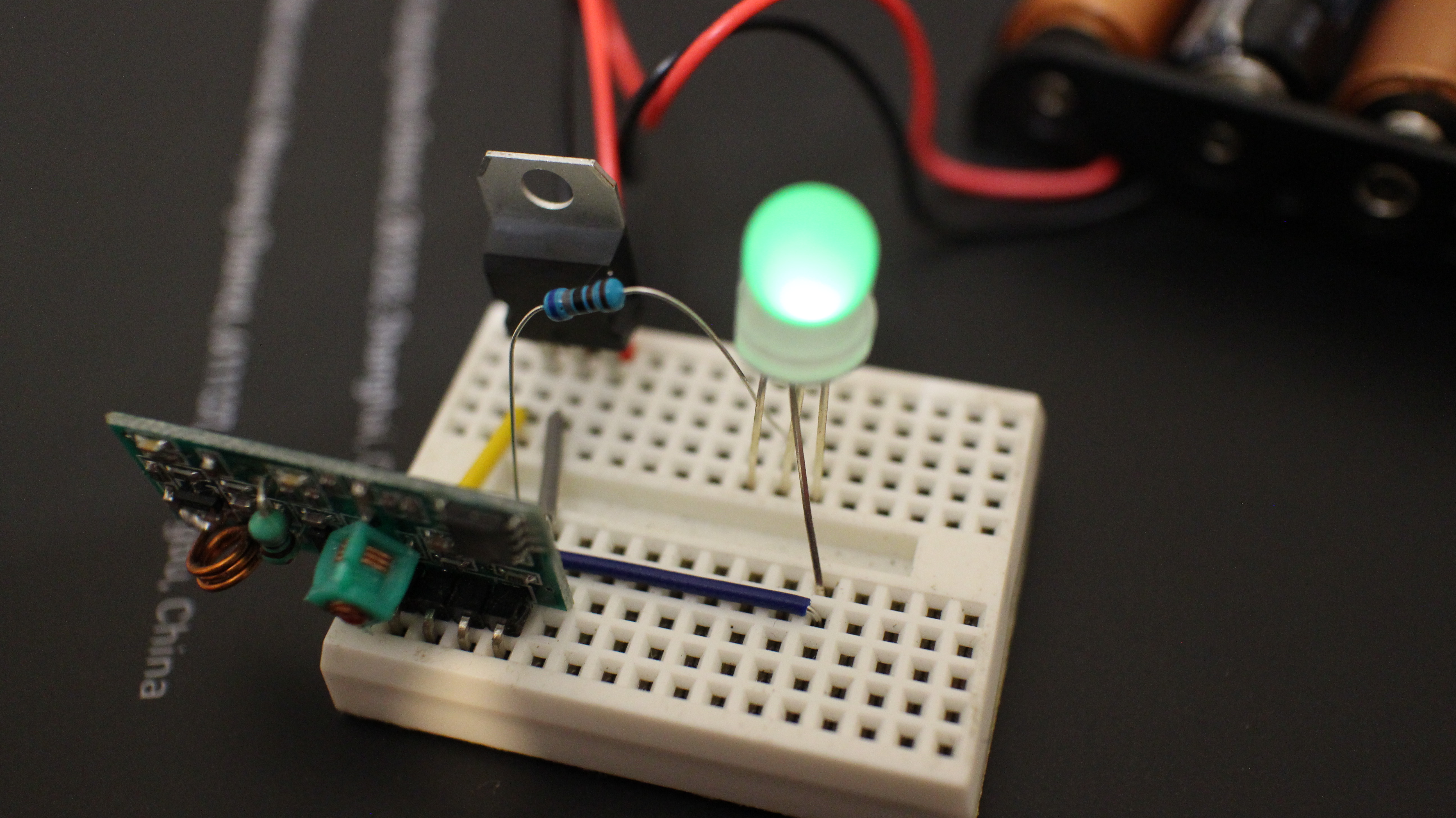
Remote jamming “detector” on the cheap
Recently, I’ve seen a number of posts on Facebook groups for South African communities about people having their car remotes jammed and the contents of their cars cleaned out while they are at petrol stations, malls and other public areas. It seems to be on the rise as an easy way for criminals to gain…